The correct preparation path is key to passing the VMware 1V0-81.20 exam. If you want to pass the Associate VMware Security exam, 1V0-81.20 dumps will be your preferred resource for preparing for the VMware 1V0-81.20 exam, which is the correct 1V0-81.20 preparation path.
Updated 1V0-81.20 dumps download it: https://www.pass4itsure.com/1v0-81-20.html Get ready for the certification exam!
What do you focus on in the VMware 1V0-81.20 exam?
Exam Full Name: Associate VMware Security
Exam Code: 1V0-81.20
Certification: VCTA-SEC 2021
language: English
Exam time: 120 minutes
Number of questions: 55
Passing Score: VMware exams are scored on a scale of 100-500, with a determined raw score range of 300
Exam Fee: $125
Skill:
- NSX-T Data Center 3.0
- Workspace ONE 20. X
- VMware Carbon Black Cloud
Official study materials:
- VMware Customer Connect Learning
- VMware Press
- VMware Certification Market Place
- VCP Community
Correct Preparation Path: pass4itsure 1V0-81.20 Dumps
How do I prepare for the Associate VMware Security exam effectively?
The following pages provide you with detailed insights to help you effectively prepare for a successful Associate VMware Security exam.
Preparing for the 1V0-81.20 exam requires the correct preparation path, and the 1V0-81.20 dumps is the correct preparation path. In particular, pass4itsure offers. You can rely on the real practice questions in pass4itsure’s 1V0-81.20 dumps to succeed on the exam.
Try it now: 1V0-81.20 free dumps, free test
Download Free 1V0-81.20 Dumps Questions: https://drive.google.com/file/d/19JfkkWCyJAvtr_zwAD0NixPnG74T9tp6/view?usp=sharing
QUESTION # 1
Which would require a Layer 7 Firewall?
A. block a specific port
B. block a subnet range
C. block a host
D. block a specific application
Correct Answer: D
QUESTION # 2
What is the default user\\’s network range when creating a new access policy rule in Workspace ONE Access?
A. 10.0.0.0/8
B. ALL RANGES
C. 192.168.0.0/16
D. LOCAL SUBNET
Correct Answer: B
QUESTION # 3
In Workspace ONE Intelligence, which of the following is a role that can be assigned to an administrator account?
A. Super User
B. Helpdesk
C. Read-only
D. Automater
Correct Answer: A
QUESTION # 4
DRAG DROP
Drag and drop the Cyber Kill events on the left into their proper sequential order on the right.
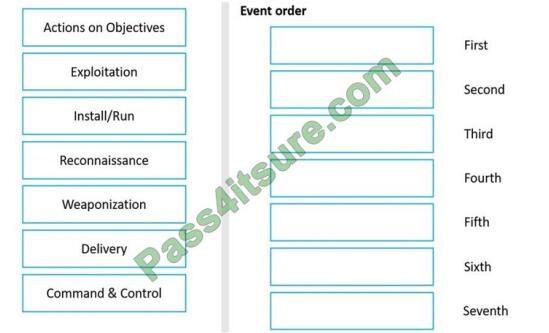
Correct Answer:

QUESTION # 5
Which is a common solution to implement for inbound network attacks?
A. Load Balancer
B. Firewall
C. Proxy
D. Reverse Proxy
Correct Answer: B
QUESTION # 6
What types of hosts are supported for hosting both NSX-T Data Center managers and host transport nodes?
A. vSphere ESXi 6.7U1 or higher, KVM on CentOS Linux
B. vSphere ESXi 6.7U1 or higher, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
C. vSphere ESXi 6.5, KVM on RHEL 7.6, Ubuntu 18.04.2 LTS
D. vSphere ESXi 6.7U1 or higher, CentOS KVM 7.6, RHEL KVM
Correct Answer: A
QUESTION # 7
What are the three core characteristics of VMware\\’s Intrinsic Security solution? (Choose three.)
A. integrated
B. extensible
C. unified
D. content-centric
E. centrally managed
F. built-in
Correct Answer: ACF
QUESTION # 8
In VMware Carbon Black Cloud, what is the search field you would use when searching for a command line?
A. command_line:
B. full_cmdline:
C. process_cmdline:
D. process_commandline
Correct Answer: D
Reference: https://docs.vmware.com/en/VMware-Carbon-Black-Cloud/services/carbon-black-cloud-userguide.pdf (29)
QUESTION # 9
Micro-segmentation is under which pillar of trust in VMware\’s 5 pillars of Zero Trust?
A. User
B. Session/Transport
C. Application
D. Device
Correct Answer: B
Reference: https://events.afcea.org/Augusta20/CUSTOM/pdf/Dell%20Technologies%20-%20ZeroTrust.pdf
QUESTION # 10
A technician has been asked to confirm a specific browser extension does not exist on any endpoint in their environment. Which is the VMware Carbon Black tool to use for this task?
A. Enterprise EDR
B. EDR
C. Audit and Remediation
D. Endpoint Standard
Correct Answer: A
QUESTION # 11
Refer to the exhibit.
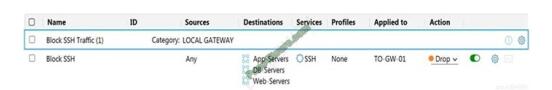
Which statement is true about the firewall rule?
A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
B. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that rejects traffic on port 22
C. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that drops traffic on port 22
D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
Correct Answer: A
QUESTION # 12
What is one of the limitations of traditional Antivirus when compared to Next Generation Antivirus?
A. Traditional AV does not need a client installed on the machines to function
B. Traditional AV focuses on signature or definition-based threats
C. Traditional AV requires integration with a SIEM to use the next-generation features
D. Traditional AV does not provide a dashboard
Correct Answer: B
QUESTION # 13
In VMware Carbon Black Cloud, which reputations have the highest priority during analysis?
A. Known Priority
B. Trusted Allow List
C. Company Allow List
D. Ignore
Correct Answer: B
For More Exam Questions For The 1V0-81.20 Exam, Please Visit this website.
Conclusion
Finally, you can conclude that preparing for the VMware 1V0-81.20 exam will be easier as long as you choose the correct preparation path – pass4itsure 1V0-81.20 dumps.