
Want to make your EC-COUNCIL (CEHv12) 312-50V12 exam perfect? Using the new 312-50V12 exam dumps and taking advantage of the updated questions and answers exercises will make you realize.
Download pass4itsure just updated new 312-50V12 exam dumps (available in both PDF and VCE options) https://www.pass4itsure.com/312-50v12.html and you can be confident that you are preparing updated questions and answers that make your preparation flawless.
pass4itsure provides up-to-date and authentic 312-50V12 mock exam questions and answers for (CEHv12) 512-50V12 exam 528+. These updated questions and answers follow the latest exam guidelines, schedules, and patterns, ensuring that you are learning the most relevant content. Here also provides free 312-50V12 questions and answers for you to practice.
Real and up-to-date insights into the Eccouncil 312-50v12 certification exam
In the ever-changing field of IT certification, success in the Eccouncil 312-50v12 exam is an important thing for individuals. As technology evolves, it’s critical to stay on top of the most up-to-date and accurate exam resources.
When it comes to preparing for the EC-COUNCIL (CEHv12) 312-50V12 exam, my thoughts are:
Find new 312-50V12 exam dumps–practice with updated questions and answers– to make the exam perfect.
Read on and you’ll be pleasantly surprised.
New 312-50V12 dumps exam questions are shared online (free)
| pass4itsure | 15/528 | More EC-COUNCIL exam questions |
Question 1:
Johnson, an attacker, performed online research for the contact details of reputed cybersecurity firms. He found the contact number of sibertech.org and dialed the number, claiming to represent a technical support team from a vendor. He warned that a specific server was about to be compromised and requested sibertech.org to follow the provided instructions.
Consequently, he prompted the victim to execute unusual commands and install malicious files, which were then used to collect and pass critical Information to Johnson\’s machine. What is the social engineering technique Steve employed in the above scenario?
A. Quid pro quo
B. Diversion theft
C. Elicitation
D. Phishing
Correct Answer: A
https://www.eccouncil.org/what-is-social-engineering/
This Social Engineering scam involves an exchange of information that can benefit both the victim and the trickster. Scammers would make the prey believe that a fair exchange will be present between both sides, but in reality, only the fraudster stands to benefit, leaving the victim hanging on to nothing. An example of a Quid Pro Quo is a scammer pretending to be an IT support technician.
The con artist asks for the login credentials of the company\’s computer saying that the company is going to receive technical support in return. Once the victim has provided the credentials, the scammer now has control over the company\’s computer and may load malware or steal personal information that can be a motive to commit identity theft.
“A quid pro quo attack (aka something for something” attack) is a variant of baiting. Instead of baiting a target with the promise of a good, a quid pro quo attack promises a service or a benefit based on the execution of a specific action.”
Question 2:
After an audit, the auditors Inform you that there is a critical finding that you must tackle Immediately. You read the audit report, and the problem is the service running on port 369. Which service Is this and how can you tackle the problem?
A. The service is LDAP. and you must change it to 636. which is LDPAPS.
B. The service is NTP. and you have to change It from UDP to TCP to encrypt it
C. The findings do not require immediate action and are only suggestions.
D. The service is SMTP, and you must change it to SMIME. which is an encrypted way to send emails.
Correct Answer: A
https://en.wikipedia.org/wiki/Lightweight_Directory_Access_Protocol LDAP, the Lightweight Directory Access Protocol, is a mature, flexible, and well-supported standards-based mechanism for interacting with directory servers.
It \ is often used for authentication and storing information about users, groups, and applications, but an LDAP directory server is a fairly general-purpose data store and can be used in a wide variety of applications. The LDAP protocol can deal with quite a bit of sensitive data: Active Directory usernames, login attempts, failed login notifications, and more.
If attackers get ahold of that data in flight, they might be able to compromise data like legitimate AD credentials and use it to poke around your network in search of valuable assets. Encrypting LDAP traffic in flight across the network can help prevent credential theft and other malicious activity, but it\’s not a failsafe–and if traffic is encrypted, your team might miss the signs of an attempted attack in progress.
While LDAP encryption isn’t standard, there is a nonstandard version of LDAP called Secure LDAP, also known as “LDAPS” or “LDAP over SSL” (SSL, or Secure Socket Layer, being the now-deprecated ancestor of Transport Layer Security). LDAPS uses its distinct network port to connect clients and servers. The default port for LDAP is port 389, but LDAPS uses port 636 and establishes TLS/SSL upon connecting with a client.
Question 3:
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure instead of SQL\’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
A. Relational, Hierarchical
B. Strict, Abstract
C. Hierarchical, Relational
D. Simple, Complex
Correct Answer: C
Question 4:
Robin, an attacker, is attempting to bypass the firewalls of an organization through the DNS tunneling method to exfiltrate data. He is using the NSTX tool to bypass the firewalls. On which of the following ports should Robin run the NSTX tool?
A. Port 53
B. Port 23
C. Port 50
D. Port 80
Correct Answer: A
DNS uses Ports 53 which is almost always open on systems, firewalls, and clients to transmit DNS queries. instead of the more familiar Transmission Control Protocol (TCP) these queries use User Datagram Protocol (UDP) due to its low latency, bandwidth, and resource usage compared to TCP-equivalent queries.
UDP has no error or flow-control capabilities, nor does it have any integrity checking to make sure the info arrived intact. How is internet use (browsing, apps, chat, etc) so reliable then? If the UDP DNS query fails (it\’s a best-effort protocol after all) within the first instance, most systems will retry a variety of times and only after multiple failures, potentially switch to TCP before trying again;
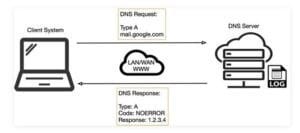
TCP is additionally used if the DNS query exceeds the restrictions of the UDP datagram size. typically 512 bytes for DNS but can depend upon system settings. Figure 1 below illustrates the essential process of how DNS operates: the client sends a question string (for example, mail. google[.]com during this case) with a particular type. typically A for a number address.
I\’ve skipped the part whereby intermediate DNS systems may need to establish where `.com\’ exists, before checking out where `google[.]com\’ are often found, and so on.
Many worms and scanners are created to seek out and exploit systems running telnet. Given these facts, it\’s no surprise that telnet is usually seen on the highest Ten Target Ports list. Several of the vulnerabilities of telnet are fixed. They require only an upgrade to the foremost current version of the telnet Daemon or OS upgrade.
As is usually the case, this upgrade has not been performed on a variety of devices. this might flow from the very fact that a lot of systems administrators and users don’t fully understand the risks involved in using telnet. Unfortunately, the sole solution for a few telnet vulnerabilities is to completely discontinue its use. The well-liked method of mitigating all of the telnet vulnerabilities is replacing it with alternate protocols like SSH.
Ssh is capable of providing many of the equivalent functions as telnet and several other additional services typically handled by other protocols like FTP and Xwindows. Ssh does still have several drawbacks to beat before it can completely replace telnet. it\’s typically only supported on newer equipment. It requires processor and memory resources to perform the info encryption and decryption.
It also requires greater bandwidth than telnet thanks to the encryption of the info. This paper was written to assist in clarifying how dangerous the utilization of telnet is often and to supply solutions to alleviate the main known threats to enhance the general security of the web Once a reputation is resolved to an IP caching also helps: the resolved name-to-IP is usually cached on the local system (and possibly on intermediate DNS servers) for a period of your time.
Subsequent queries for an equivalent name from an equivalent client then don’t leave the local system until said cache expires. Of course, once the IP address of the remote service is understood, applications can use that information to enable other TCP-based protocols, like HTTP, to try to do their actual work, for instance, ensuring internet cat GIFs are often reliably shared with your colleagues.
So, beat all, a couple of dozen extra UDP DNS queries from an organization\’s network would be fairly inconspicuous and will leave a malicious payload to beacon bent an adversary; commands could even be received by the requesting application for processing with little difficulty.
Question 5:
Gavin owns a white-hat firm and is performing a website security audit for one of his clients. He begins by running a scan which looks for common misconfigurations and outdated software versions. Which of the following tools is he most likely using?
A. Nikto
B. Nmap
C. Metasploit
D. Armitage
Correct Answer: B
Question 6:
These hackers have limited or no training and know how to use only basic techniques or tools.
What kind of hackers are we talking about?
A. Black-Hat Hackers A
B. Script Kiddies
C. White-Hat Hackers D. Gray-Hat Hacker
Correct Answer: B
Script Kiddies: These hackers have limited or no training and know how to use only basic techniques or tools. Even then they may not understand any or all of what they are doing.
Question 7:
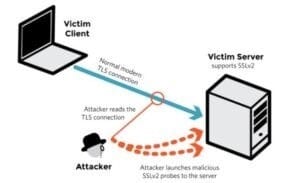
Samuel a security administrator, is assessing the configuration of a web server. He noticed that the server permits SSLv2 connections, and the same private key certificate is used on a different server that allows SSLv2 connections. This vulnerability makes the web server vulnerable to attacks as the SSLv2 server can leak key information.
Which of the following attacks can be performed by exploiting the above vulnerability?
A. DROWN attack
B. Padding oracle attack
C. Side-channel attack
D. DUHK attack
Correct Answer: A
DROWN is a serious vulnerability that affects HTTPS and other services that deem SSL and TLS, some of the essential cryptographic protocols for net security. These protocols allow everyone on the net to browse the net, use email, look online, and send instant messages while no third parties can browse the communication. DROWN allows attackers to break the encryption and read or steal sensitive communications, as well as passwords, credit card numbers, trade secrets, or financial data.
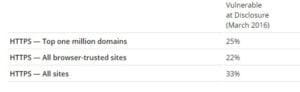
At the time of public disclosure in March 2016, our measurements indicated that two-thirds of all HTTPS servers were vulnerable to the attack. fortuitously, the vulnerability is much less prevalent currently. As of 2019, SSL Labs estimates that one.2% of HTTPS servers are vulnerable.
What will the attackers gain? Any communication between users and the server. This typically includes, however isn’t limited to, usernames and passwords, credit card numbers, emails, instant messages, and sensitive documents. under some common scenarios, an attacker can also impersonate a secure website and intercept or change the content the user sees.
Who is vulnerable? Websites, mail servers, and other TLS-dependent services are in danger from the DROWN attack. At the time of public disclosure, many popular sites were affected. we used Internet-wide scanning to determine how many sites are vulnerable:
SSLv2 Operators of vulnerable servers have to take action. there\’s nothing practical that browsers or end-users will do on their own to protect against this attack. Is my site vulnerable? Modern servers and shoppers use the TLS encryption protocol. However, because of misconfigurations, several servers also still support SSLv2, a 1990s-era precursor to TLS.
This support did not matter in practice, since no up-to-date clients use SSLv2. Therefore, even though SSLv2 is thought to be badly insecure, until now, simply supporting SSLv2 wasn’t thought of as a security problem, as clients never used it. DROWN shows that merely supporting SSLv2 may be a threat to fashionable servers and clients.
It modern associate degree attacker to modern fashionable TLS connections between up-to-date clients and servers by sending probes to a server that supports SSLv2 and uses the same private key.
SSLv2
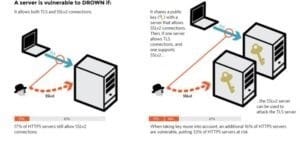
It allows SSLv2 connections. This is surprisingly common, due to misconfiguration and inappropriate default settings.
Its private key is used on any other server that allows SSLv2 connections, even for another protocol. Many companies reuse the same certificate and key on their web and email servers, for instance. In this case, if the email server supports SSLv2 and the web server do not, an attacker can take advantage of the email server to break TLS connections to the web server.
A server is vulnerable to DROWN if:
SSLv2 How do I protect my server? To protect against DROWN, server operators need to ensure that their private keys software is used anyplace with server computer code that enables SSLv2 connections. This includes net servers, SMTP servers, IMAP and POP servers, and the other software that supports SSL/TLS.
Disabling SSLv2 is difficult and depends on the particular server software. we offer instructions here for many common products: OpenSSL: OpenSSL may be a science library employed in several server merchandises. For users of OpenSSL, the simplest and recommended solution is to upgrade to a recent OpenSSL version. OpenSSL 1.0.2 users ought to upgrade to 1.0.2g.
OpenSSL 1.0.1 users ought to upgrade to one.0.1s. Users of older OpenSSL versions ought to upgrade to either one of these versions. (Updated March thirteenth, 16:00 UTC) Microsoft IIS (Windows Server): Support for SSLv2 on the server aspect is enabled by default only on the OS versions that correspond to IIS 7.0 and IIS seven.5, particularly Windows Scene, Windows Server 2008, Windows seven, and Windows Server 2008R2. This support is disabled within the appropriate SSLv2 subkey for `Server\’, as outlined in KB245030.
Although users haven’t taken the steps to disable SSLv2, the export-grade and 56-bit ciphers that build DROWN possible don’t seem to be supported by default. Network Security Services (NSS): NSS may be a common science library designed for several server merchandise.
NSS version three.13 (released back in 2012) and higher than ought to have SSLv2 disabled by default. (A small variety of users might have enabled SSLv2 manually and can take steps to disable it.) Users of older versions ought to upgrade to a more modern version. we tend to still advocate checking whether or not your non-public secret is exposed elsewhere Other affected software and in-operation systems: Instructions and data for Apache,
Postfix, Nginx, Debian, Red Hat Browsers, and other consumers: practically nothing practical that net browsers or different client computer code will do to stop DROWN. only server operators are ready to take action to guard against the attack.
Question 8:
In both pharming and phishing attacks, an attacker can create websites that look similar to legitimate sites with the intent of collecting personally identifiable information from its victims.
What is the difference between pharming and phishing attacks?
A. In a pharming attack, a victim is redirected to a fake website by modifying their host configuration file or by exploiting vulnerabilities in DNS. In a phishing attack, an attacker provides the victim with a URL that is either misspelled or looks similar to the actual website domain name
B. In a phishing attack, a victim is redirected to a fake website by modifying their host configuration file or by exploiting vulnerabilities in DNS. In a pharming attack, an attacker provides the victim with a URL that is either misspelled or looks very similar to the actual website domain name
C. Both pharming and phishing attacks are purely technical and are not considered forms of social engineering
D. Both pharming and phishing attacks are identical
Correct Answer: A
Question 9:
in this form of encryption algorithm, every Individual block contains 64-bit data, and three keys are used, where each key consists of 56 bits. Which is this encryption algorithm?
A. IDEA
B. Triple Data Encryption Standard
C. MDS encryption algorithm
D. AES
Correct Answer: B
Triple DES is another mode of DES operation. It takes three 64-bit keys, for an overall key length of 192 bits. In Stealth, you merely type within the entire 192-bit (24-character) key instead of entering each of the three keys individually. The Triple-DES DLL then breaks the user-provided key into three subkeys, padding the keys if necessary so that they are each 64-bit long.
The procedure for encryption is strictly equivalent to regular DES, but it \ is repeated 3 times, hence the name Triple DES. The info is encrypted with the primary key, decrypted with the second key, and eventually encrypted again with the third key. Triple DES runs 3 times slower than DES but is far safer if used properly. The procedure for decrypting something is that the same as the procedure for encryption, except it\’s executed in reverse.
Like DES, data is encrypted and decrypted in 64-bit chunks. Although the input key for DES is 64 bits long, the particular key employed by DES is merely 56 bits long. The smallest amount of significant (right-most) bit in each byte may be parity and will be set so that there is always an odd number of 1s in every byte.
These parity bits are ignored, so only the seven most vital bits of every byte are used, leading to a key length of 56 bits. this suggests that the effective key strength for Triple DES is really 168 bits because each of the three keys contains 8 parity bits that aren’t used during the encryption process. Triple DES ModesTriple ECB (Electronic Code Book)?
This variant of Triple DES works precisely the same way because the ECB mode of DES? is often the foremost commonly used mode of operation. Triple CBC (Cipher Block Chaining)?This method is similar to the quality DES CBC mode.?like Triple ECB, the effective key length is 168 bits, and keys are utilized equivalently, as described above, but the chaining features of CBC mode also are employed.?the primary 64-bit key acts because the Initialization Vector to DES.?Triple ECB is then executed for one 64-bit block of plaintext.?
The resulting ciphertext is then XORed with subsequent plaintext block to be encrypted, and therefore the procedure is repeated.?This method adds a layer of security to Triple DES and is therefore safer than Triple ECB, although it \ is not used as widely as Triple ECB.
Question 10:
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing “server publishing”?
A. Overloading Port Address Translation
B. Dynamic Port Address Translation
C. Dynamic Network Address Translation
D. Static Network Address Translation
Correct Answer: D
Question 11:
Your organization has signed an agreement with a web hosting provider that requires you to take full responsibility for the maintenance of the cloud-based resources. Which of the following models covers this?
A. Platform as a service
B. Software as a service
C. Functions as a
D. service Infrastructure as a service
Correct Answer: C
Question 12:
Why is a penetration test considered to be more thorough than a vulnerability scan?
A. Vulnerability scans only do host discovery and port scanning by default.
B. A penetration test actively exploits vulnerabilities in the targeted infrastructure, while a vulnerability scan does not typically involve active exploitation.
C. It is not ? a penetration test is often performed by an automated tool, while a vulnerability scan requires active engagement.
D. The tools used by penetration testers tend to have much more comprehensive vulnerability databases.
Correct Answer: B
Question 13:
Gerard, a disgruntled ex-employee of Sunglass IT Solutions, targets this organization to perform sophisticated attacks and bring down its reputation in the market. To launch the attack process, he performed DNS footprinting to gather information about ONS servers and to identify the hosts connected to the target network.
He used an automated tool that can retrieve information about DNS zone data including DNS domain names, and computer names. IP addresses. DNS records, and network Whois records. He further exploited this information to launch other sophisticated attacks. What is the tool employed by Gerard in the above scenario?
A. Knative
B. zANTI
C. Towelroot
D. Bluto
Correct Answer: D
https://www.darknet.org.uk/2017/07/bluto-dns-recon-zone-transfer-brute-forcer/ “Attackers also use DNS lookup tools such as DNSdumpster.com, Bluto, and Domain Dossier to retrieve DNS records for a specified domain or hostname. These tools retrieve information such as domains and IP addresses, domain Whois records, DNS records, and network Whois records.” CEH Module 02 Page 138
Question 14:
There are multiple cloud deployment options depending on how isolated a customer\’s resources are from those of other customers. Shared environments share the costs and allow each customer to enjoy lower operations expenses. One solution Is for a customer to Join a group of users or organizations to share a cloud environment. What is this cloud deployment option called?
A. Hybrid
B. Community
C. Public
D. Private
Correct Answer: B
The purpose of this idea is to permit multiple customers to figure out joint projects and applications that belong to the community, where it\’s necessary to possess a centralized cloud infrastructure. In other words, a Community Cloud may be a distributed infrastructure that solves the precise problems with business sectors by integrating the services provided by differing types of cloud solutions.
The communities involved in these projects, like tenders, business organizations, and research companies, specialize in similar issues in their cloud interactions. Their shared interests may include concepts and policies associated with security and compliance considerations, and therefore the goals of the project also. Community Cloud computing facilitates its users to spot and analyze their business demands better. Community Clouds could also be hosted in a data center, owned by one of the tenants, or by a third-party cloud services provider and may be either on-site or off-site.
Community Cloud Examples and Use CasesCloud providers have developed Community Cloud offerings, and a few organizations are already seeing the advantages. the subsequent list shows a number of the scenarios of the Community Cloud model that\’s beneficial to the participating organizations. Multiple governmental departments that perform transactions with each other can have their processing systems on shared infrastructure.
This setup makes it cost-effective to the tenants, and may also reduce their data traffic. Benefits of Community CloudsCommunity Cloud provides benefits to organizations within the community, individually also as collectively. Organizations don’t need to worry about the safety concerns linked with the Public Cloud due to the closed user group. This recent cloud computing model has great potential for businesses seeking cost-effective cloud services to collaborate on joint projects because it comes with multiple advantages.
Openness and ImpartialityCommunity Clouds are open systems, and they remove the dependency organizations wear cloud service providers. Organizations can achieve many benefits while avoiding the disadvantages of both public and personal clouds. Ensures compatibility among each of its users, allowing them to switch properties consistent with their individual use cases. They also enable companies to interact with their remote employees and support the utilization of various devices, be it a smartphone or a tablet.
This makes this sort of cloud solution more flexible to users\’ demands. Consists of a community of users and, as such, is scalable in several aspects like hardware resources, services, and manpower. It takes under consideration demand growth, and you simply need to increase the user base. Flexibility and ScalabilityHigh Availability and ReliabilityYour cloud service must be ready to ensure the availability of knowledge and applications in the least time.
Community Clouds secure your data in the same way as the other cloud services, by replicating data and applications in multiple secure locations to guard them from unforeseen circumstances. Cloud possesses redundant infrastructure to make sure data is out there whenever and wherever you would like it. High availability and reliability are critical concerns for any sort of cloud solution. Security and ComplianceTwo significant concerns are discussed when organizations believe cloud computing is data security and compliance with relevant regulatory authorities.
Compromising each other\’s data security isn’t profitable to anyone during a Community Cloud. the power to dam users from editing and downloading specific datasets. Making sensitive data subject to strict regulations on who has access to Sharing sensitive data unique to a specific organization would bring harm to all or any of the members involved. What devices can store sensitive data?
Users can configure various levels of security for his or her data. Common use cases: Convenience and ControlConflicts associated with convenience and control don\’t arise during a Community Cloud. Democracy may be a crucial factor the Community Cloud offers as all tenants share and own the infrastructure and make decisions collaboratively. This setup allows organizations to possess their data closer to them while avoiding the complexities of a personal Cloud.
Less Work for the IT DepartmentHaving data, applications, and systems within the cloud means you do not need to manage them entirely. This convenience eliminates the necessity for tenants to use extra human resources to manage the system. Even during a self-managed solution, the work is split among the participating organizations. Environment SustainabilityIn the Community Cloud, organizations use one platform for all their needs, which dissuades them from investing in separate cloud facilities.
This shift introduces a symbiotic relationship between broadening and shrinking the utilization of cloud among clients. With the reduction of organizations using different clouds, resources are used more efficiently, thus resulting in a smaller carbon footprint.
Question 15:
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
A. -T5
B. -O
C. -T0
D. -A
Correct Answer: A
What is the 312-50V12 exam, what is it, and what can it bring to you?
Surely you have these questions. If you want to know more about the 312-50V12 exam, I recommend this article:
The All-New C|EHv12 with New Learning Framework
It will answer you well.
New collated collections: ECCouncil 312-50v12 certification exam material
You may love the video mode
From the official video account“Know Everything: Comprehensive Guide to C|EHv12 Learning Framework: Learn, Certify, Engage & Compete” You need to take a look.
Books you may love
- Certified Ethical Hacker (CEH) v12 312-50 Exam Guide: Keep up to date with ethical hacking trends and hone your skills with hands-on activities
- CEH certified ethical hacker study guide
- Ceh: Official certified ethical hacker review guide: Exam 312-50
- CEH v9: Certified Ethical Hacker Version 9 Study Guide
- CEH v10 Certified Ethical Hacker Study Guide
- Certified Ethical Hacker (CEH) Cert Guide: Cert Ethi Hack (CEH Cert Guid
Why should many people be keen to pass the (CEHv12) 312-50V12 exam?
Because of C|EH is the most sought-after certification and is currently in short supply and in short supply worldwide. This is an opportunity for everyone!
So, you have to seize the opportunity to pass the 312-50V12 exam quickly.
Conclusion:
pass4itsure’s new 312-50V12 exam dumps https://www.pass4itsure.com/312-50v12.html include study materials and practice exercises, and provide you with flexible study options (PDF or VCE) to make the exam even better.
The effort pays off, and with the study of the new 312-50V12 exam dumps, you will pass the exam perfectly and never lag behind your skills. Now ask yourself, are you ready?
