At the end of 2025, I sat for the 350-601 DCCOR exam again and walked out with a score above 920. Not because my old cert expired. Not because HR forced me.
I did it because my day job changed.
AI clusters started landing in our data center. GPU nodes everywhere. East–west traffic exploded overnight. Designs that worked fine in 2022 suddenly felt… fragile.
When Cisco began signaling a stronger push toward AI-ready infrastructure in 2026, I realized something important:
DCCOR certification didn’t become less relevant — it became more foundational.
So this isn’t a motivational post. This is me sharing what actually helped, what tripped people up around me, and how the data center core technologies in the exam map directly to what we’re deploying today.
What Exactly Is the 350-601 DCCOR Certification?
Exam Basics (Time, Version, Format)
The 350-601 DCCOR exam is officially titled:
Implementing Cisco Data Center Core Technologies
Key facts you should know:
- Exam length: 120 minutes
- Question count: ~90–100
- Current version: v1.2 (updated May 2025)
- Format: Multiple choice, drag-and-drop, scenario-based
No simulations — but don’t underestimate the scenarios. They assume you’ve touched real gear.
Relationship with CCNP & CCIE Data Center
Here’s the clean way to think about it:
- DCCOR is mandatory for both:
- CCNP Data Center
- CCIE Data Center (written prerequisite)
Pass 350-601 DCCOR alone and you earn:
Cisco Certified Specialist – Data Center Core
Add one concentration exam, and you get CCNP Data Center.
Core Exam vs Concentration Exams
The core exam is wide and deep:
- Networking
- Compute
- Storage
- Automation
- Security
Concentration exams go narrow (design, automation, troubleshooting).
DCCOR tests whether you understand how the whole data center breathes.
2026 Exam Domain Weighting (v1.2 Blueprint)
Cisco adjusted the emphasis slightly in v1.2, but the balance is still realistic.
| Domain | Weight |
|---|---|
| Network | 25% |
| Compute | 25% |
| Storage Networking | 20% |
| Automation | 15% |
| Security | 15% |
This balance mirrors real projects. Network and compute still dominate, but automation and security are no longer “nice to have”.
Why 350-601 DCCOR Still Matters in 2026
AI-Ready Data Centers Are Changing Everything
Gartner projects that by 2026, 80% of enterprise data centers will need to support AI workloads.
What does that mean in practice?
- Massive east–west traffic
- Lossless fabrics
- Automation-first operations
- Tight security boundaries
The 350-601 DCCOR certification covers the exact core skills needed to survive that shift.
Real-World Job & Salary Impact
From what I’ve seen (and Glassdoor backs this up):
- CCNP Data Center holders average 15–20% higher pay
- Roles unlocked:
- Data Center Architect
- Cloud Networking Engineer
- Infrastructure Automation Engineer
This isn’t an “old-school” cert. It’s the base layer for modern infrastructure.
Blueprint Changes You Can’t Ignore (v1.1 → v1.2)
Cisco didn’t rewrite the exam — they refined it.
Key shifts:
- More hybrid cloud awareness
- Stronger focus on programmability
- Automation scenarios feel more real
- Less memorization, more reasoning
If you studied years ago, your knowledge isn’t wrong — just incomplete.
Deep Dive: Network Domain (25%)
NX-OS Fundamentals
You need to understand:
- vPC behavior
- OSPF vs BGP use cases
- Control-plane vs data-plane separation
Common trap ❗
People memorize commands but don’t understand why NX-OS behaves differently from IOS.
VXLAN & EVPN
This is no longer optional knowledge.
You should be comfortable with:
- VXLAN encapsulation
- EVPN control plane
- Anycast gateways
Real-world note:
If you’ve deployed ACI, VXLAN concepts suddenly click.
ACI Real-World Configuration
Know the logic, not every click:
- Tenants
- VRFs
- Bridge Domains
- Contracts
✅ Exam loves “why traffic is blocked” scenarios.
Deep Dive: Compute Domain (25%)
UCS Architecture Essentials
Understand:
- Fabric Interconnect roles
- Service profiles
- Stateless computing
B-Series vs C-Series
Quick rule of thumb:
- B-Series → density, blade environments
- C-Series → flexibility, standalone or rack
Trap ❗
Mixing management models in answers.
Deep Dive: Storage Networking (20%)
Fibre Channel Basics
You must know:
- Zoning types
- VSAN concepts
- FLOGI vs PLOGI
FCoE & SAN Pitfalls
Cisco loves asking:
“Why is traffic dropping even though links are up?”
Answer often involves:
- Lossless Ethernet
- DCB misconfiguration
Deep Dive: Automation (15%)
Ansible Basics for DCCOR
You’re not writing full playbooks, but you must know:
- YAML structure
- Idempotency
- Modules vs roles
Python & APIs
Focus on:
- REST APIs
- JSON structure
- Authentication tokens
Automation is about intent, not syntax.
Deep Dive: Security (15%)
RBAC
Know:
- Role separation
- Least privilege
- UCS & ACI role models
Zero Trust in the Data Center
Expect conceptual questions:
- Microsegmentation
- Policy-based access
- East–west security
My High-Score (920+) Study Path
My approach was simple:
- 3 months
- Short daily sessions
- Hands-on whenever possible
Resources I used:
I also practiced with pass4itsure 350-601 materials. The explanations helped me spot blueprint changes fast.
👉 https://www.pass4itsure.com/350-601.html
Low-Cost Lab Strategy That Actually Works
You don’t need a full rack.
What worked:
- EVE-NG for topology logic
- Cisco dCloud for ACI/UCS
- Whiteboarding traffic flows
If you can explain a packet’s journey, you can answer the question.
High-Frequency 350-601 DCCOR Exam Practice Area (2026 Blueprint)
Theory alone won’t cut it.
I compiled 15 high-frequency DCCOR practice scenarios aligned with the 2026 blueprint:
- Each question targets a common failure point
- Full explanations
- Real deployment context
Question 1:
Refer to the exhibit.
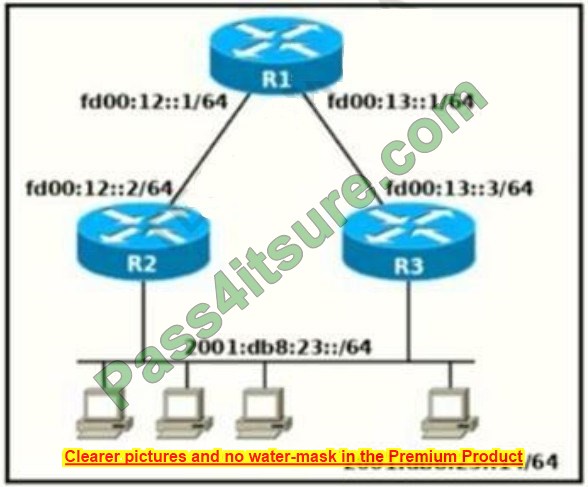
A Cisco data center environment is implemented with vPC.
The web server replies using the SVI MAC address as the Layer 2 header instead of the HSRP MAC address on VLAN 23.
This behavior causes packet drops on the Cisco Nexus 9000 Series Switches due to the vPC loop prevention mechanism.
The requirement is for the vPC feature to allow N9K_1 and N9K_2 to forward traffic between the NAS server and the web server, even if the HSRP\’s MAC address is not used on Layer 2 headers for VLAN 23.
Which feature must be used to accomplish this goal?
A. ARP Sync
B. Object Tracking
C. L3 Peer Router
D. Peer Gateway
Correct Answer: D
Explanation
In vPC environments, the loop prevention mechanism drops packets that arrive on the vPC peer-link with a source MAC belonging to the peer switch (to avoid potential loops). Here, the web server is sending replies using the SVI MAC of one Nexus switch (instead of the HSRP virtual MAC) on VLAN 23. When these packets cross the peer-link, the receiving peer detects its own SVI MAC as the destination and drops them.
The peer-gateway feature resolves this by allowing both vPC peers to forward traffic destined to each other’s router MAC addresses (including SVI MACs). Once enabled, N9K_1 and N9K_2 can properly forward traffic between the NAS and web server, even when the HSRP virtual MAC is bypassed.
Why not the others:
- A. ARP Sync: Only synchronizes ARP tables between peers; does not address MAC forwarding issues.
- B. Object Tracking: Used for HSRP/VRRP failover based on interface or route state; unrelated to L2 MAC handling.
- C. L3 Peer Router: Enables routing protocol adjacency over vPC VLANs; not relevant to this L2 forwarding problem.
Blueprint link: 1.3 Network (vPC peer-gateway configuration and behavior).
Real-world note: Common in setups where servers use direct SVI routing instead of default gateway with HSRP virtual MAC. Enable with peer-gateway under the vPC domain—simple fix, no downtime.
Question 2:
Which Cisco UCS Manager XML encoded backup type must be used to back up user names, roles, and service profiles?
A. Full State Configuration
B. Logical Configuration
C. All Configuration
D. System Configuration
Correct Answer: C
Explanation
The All Configuration backup is an XML-encoded export that captures the complete UCS domain configuration, including administrative elements (user accounts, roles, locales), logical elements (service profiles, policies, pools, templates), and system settings. This makes it the only type that fully backs up user names, roles, and service profiles in one file.
Why not the others:
- A. Full State Configuration: Binary (not XML) backup for exact runtime state (firmware, adapter settings, hardware inventory); used for disaster recovery on identical hardware, excludes logical/admin configs like users/roles.
- B. Logical Configuration: XML export of only logical elements (service profiles, policies, UUID/Serial pools); explicitly excludes users, roles, and locales.
- D. System Configuration: XML export limited to basic system settings (DNS, NTP, call home, management interfaces); no users, roles, or service profiles.
Blueprint link: 2.0 Compute (UCS Manager backup and import operations, configuration export types).
Real-world note: Choose All Configuration when migrating domains or preserving RBAC/user data. Export via GUI (Admin > All Configuration) or CLI (scope org / ; export-config), then import selectively if needed.
Question 3:
The network team needs permissions to access the Cisco UCS B-Series Servers via the Cisco UCS Manager GUI to configure the network and collect information about faults.
The administrator wants to assign these permissions to the newly configured user called netops.
Which set of tasks must the administrator perform to accomplish these goals?
A. Implement username netops on the locally authenticated user. Assign the roles of network administrator and operations.
B. Configure username netops on the Cisco UCS Manager login profile. Assign the roles of AAA administrator and operations.
C. Enable username netops on the authenticated users. Assign the roles of storage administrator and facility manager.
D. Deploy username netops on the users locales. Assign the roles of networks security and facility manager.
Correct Answer: A
Explanation
In Cisco UCS Manager, local users are created under Admin > User Management > Local Users. Assign predefined roles like “network-administrator” (for configuring vNICs, LAN policies, QoS, etc.) and “operations” (for viewing faults, statistics, logs, and basic read-only access). This exactly matches the requirement for network config and fault info access without granting excessive privileges.
Why not the others:
- B. AAA administrator: Controls authentication settings (LDAP/RADIUS); no network or fault access.
- C. Storage administrator: Limited to SAN/storage policies; facility-manager is unrelated (physical access control).
- D. Networks security: Not a valid role; locales restrict org access but roles are assigned separately—no “networks security” or “facility manager” for this goal.
Blueprint link: 2.0 Compute (UCS Manager user management, RBAC roles and privileges).
Real-world note: Always use least-privilege—combine network-administrator + operations for netops teams. Create via GUI (Users > Create User > Assign Roles) or CLI (create user netops ; set role network-administrator ; set role operations). Test login after.
Question 4:
A network engineer must create an EEM script that saves a copy of the running configuration on bootflash and writes a message to syslog when a user saves the configuration to a Cisco Nexus switch.
Which configuration set should be applied to complete this task?
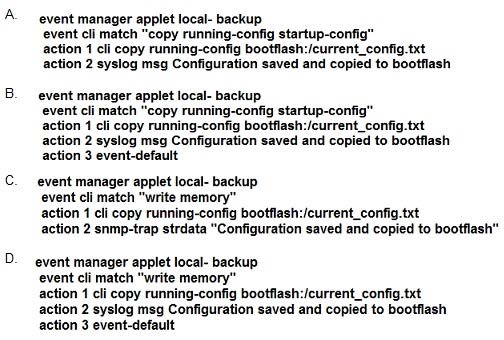
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
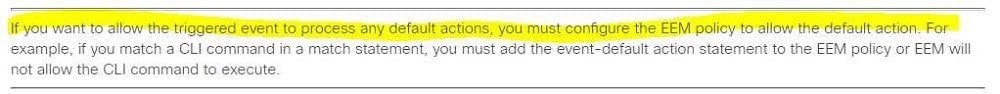
Explanation
The command write memory is not valid in NX-OS The “event-default”
Question 5:
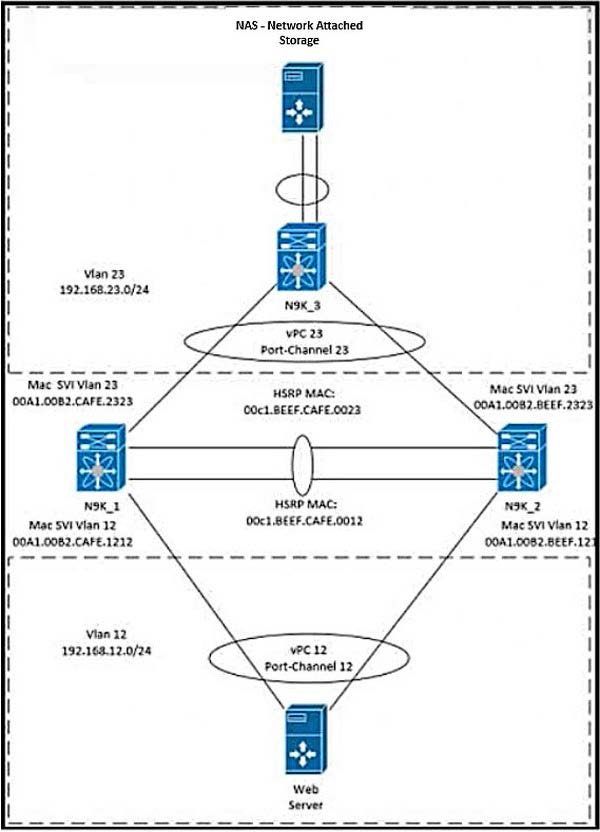
An engineer must perform backup and restore of the Cisco UCS Manager configuration.
The configuration must be stored on a remote server via XML encoding.
The backup must store the configurations of the chassis. FEX, rack servers. lOMs, and blade server.
Which set of actions accomplishes these goals?
A. Perform a logical configuration backup and run the replace import method.
B. Perform a ful state configuration backup and run the restore procedure.
C. Perform a system configuration backup and run the merge import method
D. Perform an all configuration backup and run the system restore procedure.
Correct Answer: C
Explanation
System Configuration backup is XML-encoded and specifically captures infrastructure elements like chassis discovery policies, FEX, IOMs, rack-mount servers, and blade server configurations (acknowledgment, decommissioning, etc.). It can be exported to a remote server (TFTP/SCP/etc.). The merge import method safely overlays these settings during restore without disrupting unrelated configs.
Why not the others:
- A. Logical Configuration: XML but only logical elements (service profiles, policies, pools); excludes chassis/FEX/IOM/rack/blade hardware configs.
- B. Full State: Binary (not XML), includes runtime state for exact restore on identical hardware; no selective import.
- D. All Configuration: XML and broadest (logical + system + admin); overkill here, and “system restore” is not the standard term—typically merge/replace.
Blueprint link: 2.0 Compute (UCS Manager backup types, export/import methods for infrastructure configuration).
Real-world note: Use System Config for hardware inventory migrations or discovery policy backups. Export via GUI (Admin > System Configuration) or CLI (export-config system), then import with merge to avoid overwriting logical configs.
Question 6:
A Cisco ACI engineer must configure an access port on a Cisco ACI leaf switch.
The access policy should be configured so that it supports L3Out connectivity concurrently with several EPGs that are mapped to this interface with the static port method.
How should the access policy be configured?
A. by linking the interface policy group to multiple Attachable Access Entity Profiles
B. with two interface policy groups that are linked to the same interface profile port selector
C. by mapping a single physical domain, mapped to the L3out and EPG interfaces
D. with a single Attachable Access Entity Profile that is linked to the corresponding routed domain and physical domain
Correct Answer: D
Explanation
To share a single physical access port for both L3Out (routed/subinterface connectivity) and multiple static-bound EPGs (different VLAN encap), configure a single Attachable Access Entity Profile (AAEP). Associate this AAEP with both a Physical Domain (for EPG static port bindings and VLAN pool) and an L3 Domain (for the L3Out). The interface policy group then references this AAEP, allowing concurrent use without conflicts.
Why not the others:
- A. Multiple AAEPs: Interface policy groups link to one AAEP; multiple would require separate policy groups/selectors, not supported for concurrent on the same port.
- B. Two interface policy groups: Requires separate port selectors or overrides; not for simultaneous L3Out + EPG static bindings on one port.
- C. Single physical domain: PhysDom only handles access/EPG VLANs; L3Out requires an L3 Domain profile for external routing.
Blueprint link: 1.0 Network (ACI access policies, AAEPs, domain associations, static port binding with L3Out).
Real-world note: Ideal for border leaf ports needing tenant access + external connectivity (e.g., shared infra). Create AAEP > attach PhysDom + L3Dom > link to interface policy group > apply to leaf interface. Validate with “show endpoints” and routing tables post-deploy.
Question 7:
Cisco Nexus 9000 Series Switches are configured with LACP protocol and default aging timers.
What is the impact on the LACP peer during an ISSU upgrade?
A. The LACP peer connection terminates.
B. The LACP peer session remains up.
C. The LACP peer renegotiates the adjacency.
D. The LACP peer connection resets.
Correct Answer: B
Explanation
Nexus 9000 ISSU is designed to be non-disruptive for control plane protocols. With default LACP timers (30s hello, 90s timeout), the upgrade process maintains stateful switchover; LACP PDUs continue across the peer-link or member ports, preventing timeout. The peer session stays up without flaps or renegotiation.
Why not the others:
- A/C/D: Wrong—ISSU avoids control plane restarts that would terminate, reset, or force renegotiation of LACP. Only disruptive upgrades (e.g., reload) or misconfigured timers cause flaps.
Blueprint link: 1.0 Network (LACP operation, timers, and ISSU impact on port-channels/vPC).
Real-world note: Common in production vPC setups—verify with show lacp neighbor pre/post-ISSU; no traffic loss if vPC role doesn’t change. Use lacp suspend-individual if needed for edge cases.
Question 8:
Refer to the exhibit.
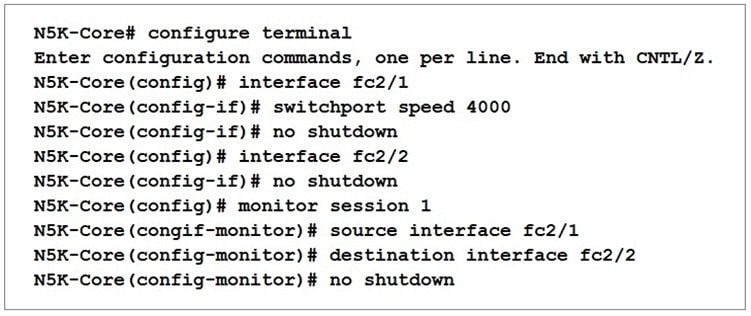
An engineer implements SPAN configuration on an Nexus 5000 series switch.
Which two commands are necessary to complete the SPAN session configuration?
A. Configure the switchport monitor under interface fc2/2
B. Configure the switchport mode SD under interface tc2/1.
C. Configure switchport speed 4000 under interface fc2/2.
D. Configure session type fc under monitor session 1.
E. Configure the switchport mode SD under interface fc2/2.
Correct Answer: CE
Explanation
On Nexus 5000, Fibre Channel SPAN (local) requires the destination port (fc2/2) to be dedicated as a SPAN destination with switchport mode SD. The destination port speed must also match the source (here 4000) to avoid session errors or drops—hence switchport speed 4000 on fc2/2 completes the setup.
Why not the others:
- A. switchport monitor: Ethernet SPAN command; not used for FC ports on N5K.
- B. switchport mode SD on fc2/1: Wrong interface—source ports remain in default mode (E/F); only destination needs SD.
- D. session type fc: Not required on N5K (implicit for FC); used on later platforms (e.g., N9K with mixed traffic).
Blueprint link: 1.0 Network (SPAN/RSPAN/ERSPAN configuration on Nexus platforms, FC-specific requirements on N5K).
Real-world note: Always dedicate SD ports—no production traffic allowed. Verify with show monitor session 1 after config; session stays down if speed mismatches or mode SD missing. Common in FC troubleshooting setups.
Question 9:
An engineer must automate the provisioning of Cisco ACI objects using the Terraform tool.
The engineer must ensure that APIC counts the authentication login requests against the threshold to avoid a DOS attack.
Which configuration must be used in Terraform to accomplish these goals?
A. resources with user ID and password
B. resources with signature-based authentication
C. provider with user ID and password
D. provider with signature-based authentication
Correct Answer: C
Explanation
Terraform ACI provider handles authentication at the provider level. Configuring username and password in the provider block triggers standard APIC login requests, which APIC counts against its failed/successful login threshold (default 5 attempts). This enforces the built-in DoS protection mechanism by potentially locking the user after excessive logins.
Why not the others:
- A/B: Authentication is never set in individual resources; it’s provider-scoped.
- D. provider with signature-based authentication: Uses private_key and cert_name for signed requests—no login attempts are counted, bypassing the threshold (recommended for automation to prevent lockouts).
Blueprint link: 4.0 Automation (ACI Terraform provider configuration, authentication impacts).
Real-world note: Username/password suits low-frequency use where DoS protection via threshold is prioritized. For CI/CD, switch to signature-based in provider block to avoid lockouts—documented in official Terraform ACI provider docs.
Question 10:
An engineer must generate a checkpoint of the running configuration on a Cisco Nexus Switch.
The checkpoint file name must be called “before_maintenance\’ and should be used for recovering the switch to its pre-maintenance state.
The rollback of the checkpoint to running configuration should only occur if no errors occur.
Which two configuration commands must be used to meet these requirements? (Choose two.)
A. rollback checkpoint file before_maintenance stop-at-first-failure
B. checkpoint file before_maintenance
C. checkpoint before_maintenance
D. rollback running-config file before_maintenance atomic
E. rollback running-config checkpoint before_maintenance
Correct Answer: BD
Explanation
To create a file-based checkpoint named “before_maintenance”, use checkpoint file before_maintenance—this stores the running config as a rollback point. For safe rollback (commit only if no errors, revert entirely on failure), use rollback running-config file before_maintenance atomic—the “atomic” keyword ensures error-free application.
Why not the others:
- A: Invalid syntax—”rollback checkpoint file” is not a command; stop-at-first-failure is an older option, superseded by atomic.
- C: Creates a named (not file-based) checkpoint; doesn’t match the “file” requirement.
- E: Correct for named checkpoints but wrong syntax for file-based; missing “atomic” allows partial application on errors.
Blueprint link: 1.0 Network (Nexus configuration management, checkpoints, atomic rollback).
Real-world note: File-based checkpoints are stored in bootflash: and ideal for scripted maintenance. Always verify with show checkpoint summary before/after; atomic prevents partial configs during rollback.
Question 11:
Refer to the exhibit.
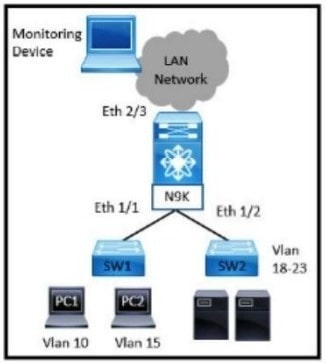
A network administrator experiences these issues with the network:
PC1 is experiencing a buffering problem for video applications The servers that are connected to SW2 are experiencing packet drops when they connect to the Internet The engineer wants to configure the required traffic capture to investigate the issue further Which configuration must be implemented to monitor the traffic?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
Explanation
Option D configures SPAN source as VLAN 10 rx (captures ingress traffic specifically from PC1 in VLAN 10) and interface Eth1/2 (bidirectional by default, capturing to/from servers in VLANs 18-23). This precisely targets traffic originating from the affected devices—PC1 (for video buffering investigation, e.g., its outbound requests/patterns) and servers (for packet drops to Internet, capturing their outbound flows)—minimizing irrelevant data on the monitor port.
Why not the others:
- A: Sources both Eth1/1 and Eth1/2 (likely bidirectional/rx), includes unnecessary traffic from/to PC2 in VLAN 15, overloading the capture.
- B: Tx-focused session captures traffic sent to the endpoints, not from them; misses client-originated packets key to diagnosing send-side issues/drops.
- C: Sources VLAN 10-15 rx (includes irrelevant PC2 traffic) plus Eth1/2; overcaptures non-problematic flows.
Blueprint link: 1.0 Network (Nexus SPAN sources: VLAN vs interface, direction for targeted monitoring).
Real-world note: VLAN rx sourcing isolates specific host traffic efficiently on access layers. Use Wireshark filters on the monitoring device for deeper analysis; check session status with show monitor session all.
Question 12:
A customer reports Fibre Channel login requests to a Cisco MDS 9000 Series Switch from an unauthorized source.
The customer requires a feature that will allow all devices already logged in and learned to be added to the Fibre Channel active database.
Which two features must be enabled to accomplish this goal? (Choose two.)
A. auto-learning
B. smart aliases
C. port security
D. enhanced zoning
E. device aliases
Correct Answer: AC
Explanation
Port security on MDS restricts FC logins to authorized WWNs per port/zone. Enabling auto-learning (under port security) automatically detects and adds currently logged-in devices to the active security database, then locks down future unauthorized logins—exactly meeting the requirement to preserve existing sessions while blocking new unauthorized ones.
Why not the others:
- B. Smart aliases: Advanced device alias distribution mode; naming only, no login control.
- D. Enhanced zoning: Strengthens zone enforcement (e.g., session-based checks); prevents unauthorized sessions but doesn’t auto-populate existing devices into a database.
- E. Device aliases: Simplifies WWN naming in zones; unrelated to login authorization or auto-learning.
Blueprint link: 3.0 Storage Network (MDS port security, auto-learn feature for FC login control).
Real-world note: Configure with port-security activate auto-learn on the VSAN; verify with show port-security database active. Commit changes carefully to avoid lockouts—common in migrations or audits.
Question 13:
What is the impact of a nondisruptive upgrade on fabric and modular switches?
A. The upgrade disrupts the control plane for more than 120 seconds.
B. During the upgrade, new devices cannot log in to the fabric.
C. If a zone server merge is in progress, the upgrade continues without interruption.
D. When the installation is complete, the system BIOS must be updated.
Correct Answer: B
Explanation
During a nondisruptive ISSU on Cisco MDS 9000 fabric/modular switches, the upgrade process temporarily blocks new FLOGI/PLOGI requests to maintain fabric stability and prevent inconsistencies across the VSAN during switchover. Existing device logins and active I/O remain unaffected.
Why not the others:
- A: Nondisruptive upgrades ensure control plane disruption is minimal (typically <120 seconds or hitless in supported setups).
- C: Pending operations like zone set merges must complete before upgrade; the process aborts or pauses if conflicts exist.
- D: BIOS/firmware updates are manual/separate; not required post-software upgrade.
Blueprint link: 3.0 Storage Network (MDS nondisruptive ISSU, fabric login behavior during upgrade).
Real-world note: Verify with show install all impact pre-upgrade; new logins auto-resume after completion. Common in production SANs to avoid outages.
Question 14:
Which method must a network engineer use to upgrade the BIOS firmware of a Cisco UCS standalone C- Series reck-mount server?
A. Use the Cisco host upgrade utility.
B. Use the Cisco hardware upgrade utility.
C. Use the Cisco host firmware policy.
D. Use the U-ACPI Interface.
Correct Answer: A
Explanation
The correct method is Cisco Host Upgrade Utility (HUU) because a standalone Cisco UCS C-Series rack server is not managed by UCS Manager.
HUU is designed specifically to update system components such as BIOS, CIMC, RAID controller, and adapters on standalone servers through a bootable ISO.
The other options apply to UCS Manager–managed environments or are not valid tools for BIOS upgrades on C-Series standalone servers.
Question 15:
An engineer is configuring a vHBA template in UCS Manager.
The engineer needs to specify the logical addresses used by the vHBA and the path through which the SAN traffic flows.
Which two resources must be specified in the vHBA template? (Choose two.)
A. MAC addresses
B. WWPNPool
C. WWNN
D. VLAN ID
E. Fabric ID
Correct Answer: BE
Explanation
In a vHBA template, the engineer must define WWPN Pool to assign the virtual HBA’s Fibre Channel identity, which provides the logical addressing required for SAN communication.
The Fabric ID is also required because it determines whether the vHBA connects through Fabric A or Fabric B, defining the SAN traffic path.
MAC addresses and VLAN IDs are Ethernet-related, and WWNN is defined at the service profile level, not in the vHBA template.
…
Where Data Center Careers Are Headed
The data center isn’t dying.
It’s mutating.
AI, automation, zero trust — all roads still pass through the core. The 350-601 DCCOR exam doesn’t just test knowledge. It validates whether you understand how modern infrastructure actually works.
If you’re studying now, you’re not late. You’re right on time.
FAQs
1. Is 350-601 DCCOR hard for experienced engineers?
Yes — but for different reasons. Breadth, not depth.
2. How long should I study for DCCOR?
2–4 months if you’re hands-on already.
3. Is automation heavily tested?
Yes. Especially conceptual understanding.
4. Can I pass without real ACI experience?
Possible, but labs help massively.
5. Is DCCOR still relevant with AI-focused certs coming?
Absolutely. It’s the foundation those certs build on.